
Looters' arrest uncovers 2,000-year-old workshop near Jerusalem biblical pilgrimage path
Uncovering a 2,000-year-old stone vessel workshop that once served pilgrims, Israeli authorities caught antiquity thieves red-handed in Jerusalem cave.

Uncovering a 2,000-year-old stone vessel workshop that once served pilgrims, Israeli authorities caught antiquity thieves red-handed in Jerusalem cave.

Cybersecurity researchers have disclosed details of a new Android trojan called Massiv that's designed to facilitate device takeover (DTO) attacks for financial theft. The malware, according to ThreatFabric, masquerades as seemingly harmless IPTV apps to dece…

Cybersecurity researchers have disclosed details of a new mobile spyware platform dubbed ZeroDayRAT that's being advertised on Telegram as a way to grab sensitive data and facilitate real-time surveillance on Android and iOS devices. "The developer runs dedic…

Large stone tool workshop from the Second Temple period, which produced tools for Jews some 2,000 years ago, uncovered in a cave on the eastern slopes of Mount Scopus in Jerusalem.
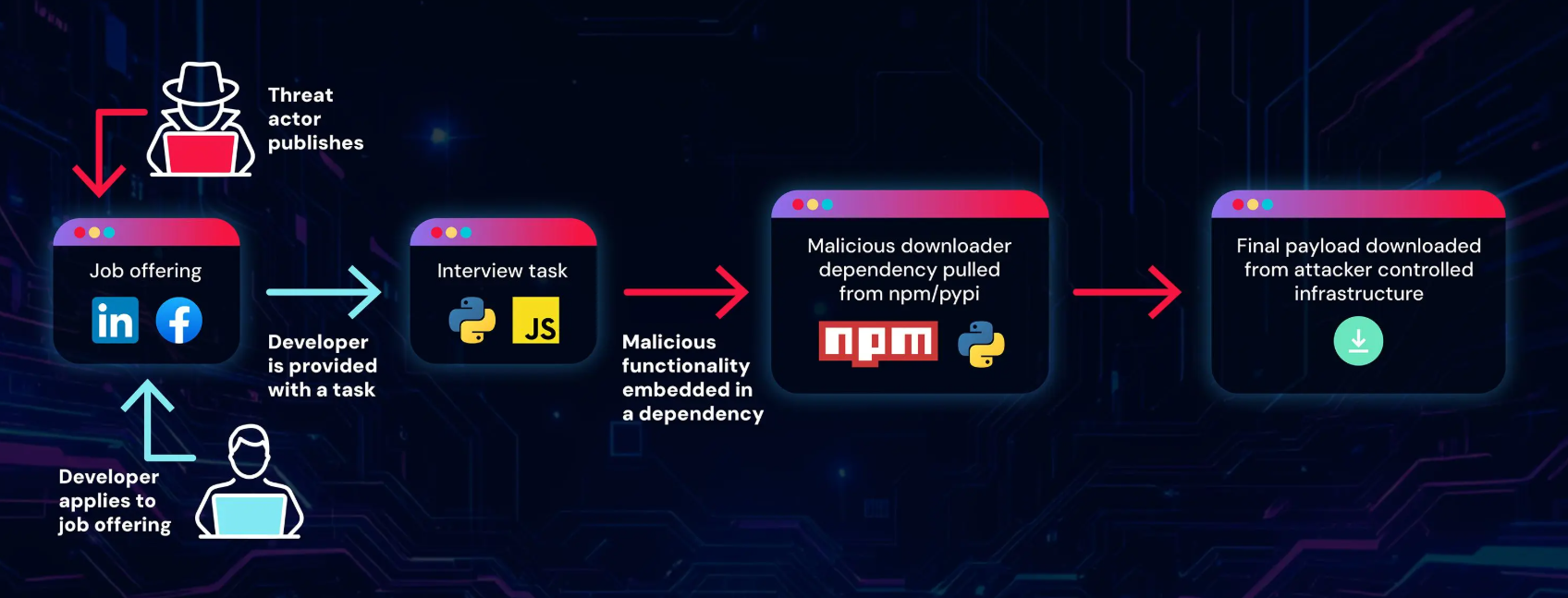
Researchers found malicious npm and PyPI packages tied to a fake recruitment campaign linked to North Korea’s Lazarus Group. ReversingLabs researcher uncovered new malicious packages on npm and PyPI connected to a fake job recruitment campaign attributed to t…

Cybersecurity researchers have discovered a fresh set of malicious packages across npm and the Python Package Index (PyPI) repository linked to a fake recruitment-themed campaign orchestrated by the North Korea-linked Lazarus Group. The coordinated campaign h…

Campaign combines stolen Telegram accounts, fake Zoom calls and ClickFix attacks to deploy infostealer malware

The North Korea-linked threat actor known as UNC1069 has been observed targeting the cryptocurrency sector to steal sensitive data from Windows and macOS systems with the ultimate goal of facilitating financial theft. "The intrusion relied on a social enginee…

Romance scams are among the most emotionally damaging forms of cyber crime because they combine carefully manufactured intimacy with financial theft – the scammers go after your heart, and then your wallet.

In the lead up to Valentine’s Day, dating apps get busier – and so do scammers.

The Mandiant security team says North Korean hackers are upgrading their social engineering tactics to include AI-generated video.
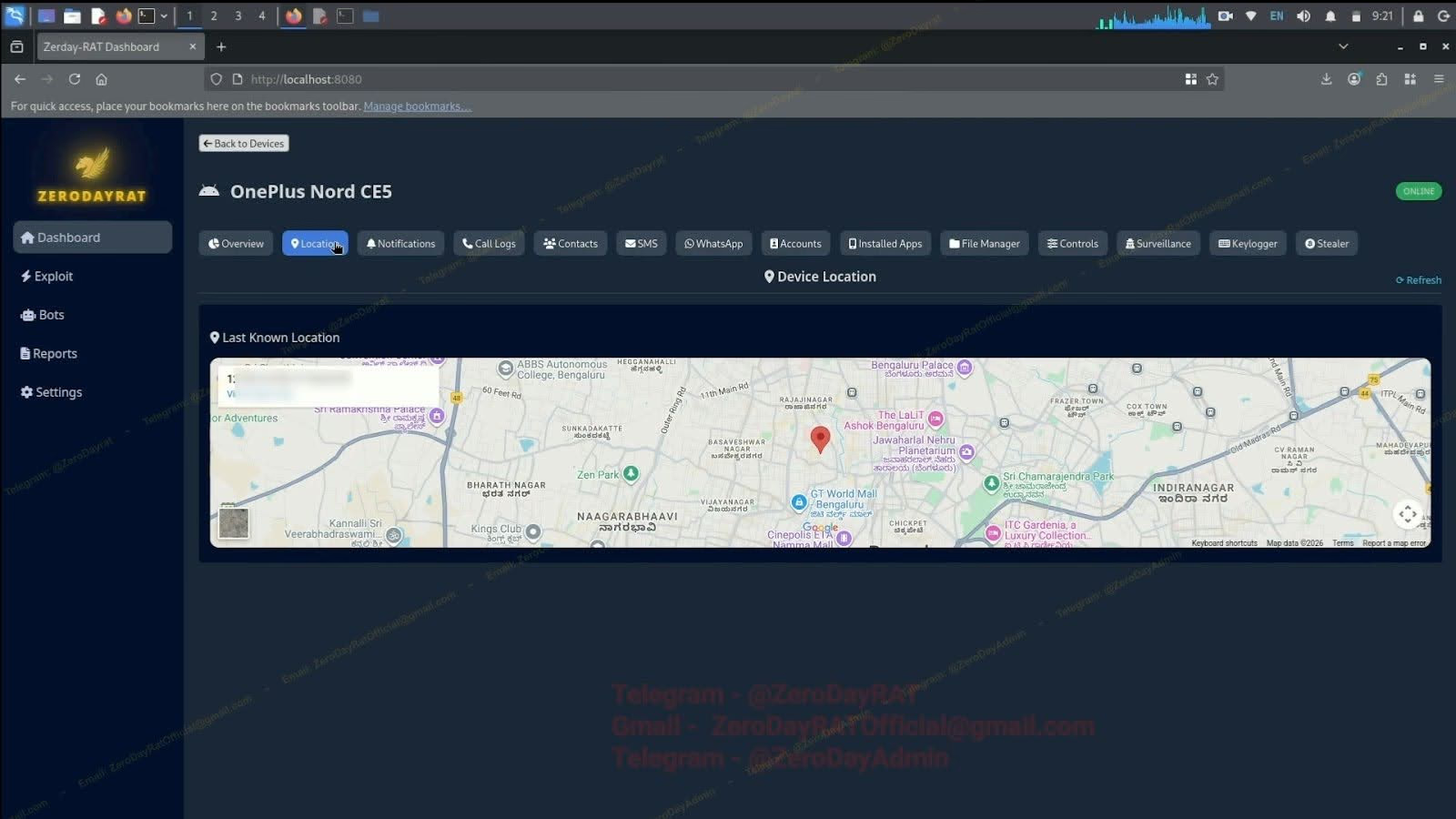
ZeroDayRAT is a commercial mobile spyware that grants full remote access to Android and iOS devices for spying and data theft. ZeroDayRAT is a newly discovered commercial mobile spyware toolkit that gives attackers full control over Android and iOS devices. I…

ZeroDayRAT is a new mobile spyware targeting Android and iOS, offering attackers persistent access

ZeroDayRAT is a new spyware sold on Telegram that targets Android and iOS devices with live surveillance, keylogging, and financial theft.

A new commercial mobile spyware platform dubbed ZeroDayRAT is being advertised to cybercriminals on Telegram as a tool that provides full remote control over compromised Android and iOS devices. [...]

Microsoft warns info-stealing attacks are expanding from Windows to macOS, using cross-platform languages like Python and abusing trusted platforms. Microsoft warns info-stealing attacks are rapidly expanding from Windows to macOS, using cross-platform langua…
None
High Vulnerabilities <table> <tr> <th>PrimaryVendor -- Product</th> <th>Description</th> <th>Published</th> <th>CVSS Score</th> <th>Source Info</th> <th>Patch Info</th> </tr> <tr> <td>Agatasoft--AgataSoft PingMaster Pro</td> <td>AgataSoft PingMaster Pr…

As many as 3,136 individual IP addresses linked to likely targets of the Contagious Interview activity have been identified, with the campaign claiming 20 potential victim organizations spanning artificial intelligence (AI), cryptocurrency, financial services…

In cybersecurity, the line between a normal update and a serious incident keeps getting thinner. Systems that once felt reliable are now under pressure from constant change. New AI tools, connected devices, and automated systems quietly create more ways in, o…

Microsoft’s investigation into RedVDS services and infrastructure uncovered a global network of disparate cybercriminals purchasing and using to target multiple sectors. In collaboration with law enforcement agencies worldwide, Microsoft’s Digital Crimes Unit…
NEW HAVEN, Conn. (WTNH) — New Haven Police Chief Karl Jacobson admitted theft and misuse of public funds, Mayor Justin Elicker announced during a press conference Monday. Jacobson allegedly admitted to taking money from a city fund used for confidential infor…

North Korea’s Lazarus Group deploys a new BeaverTail variant to steal credentials and crypto using fake job lures, dev tools, and smart contracts.

A new variant of the BeaverTail malware linked to North Korean hackers has been identified targeting cryptocurrency traders and developers

SimpleX Chat’s X account hacked to promote fake crypto site urging users to connect wallets. Site mimicked official design to steal funds.